Revolutionize Your
Document Capture
Transition from cluttered cabinets to streamlined digital solutions—effortlessly.
Welcome to
Spectrum Information Services,
where transforming paper chaos into streamlined digital solutions is our expertise. Explore how our document scanning and management services can revolutionize your operations, ensuring nothing holds back your progress.
Our Services
Why Choose Us
Unmatched Quality
and Expertise
Leading with cutting-edge
technology since 1991,
we ensure your documents are
managed with top-tier quality.

Integrity and
Security
We adhere to strict federal
regulations, ensuring your data's
security while surpassing
expectations with unwavering integrity.

Dedicated Client
Satisfaction
Our team is committed to
superior outcomes and empowering
your staff, enhancing your
experience and independence.
What We Do
DIGITAL TRANSFORMATION. We help organizations reduce cost by improving how they work with documents. This includes a wide range of scanning services and software solutions.

What We Do
DIGITAL TRANSFORMATION. We help organizations reduce cost by improving how they work with documents. This includes a wide range of scanning services and software solutions.
Why We Do It
FACT: DISASTERS HAPPEN.
How would your organization recover if a major disaster or data breech compromised your physical records?
A major disaster or data breach could compromise your physical records, and industry research shows that about 20% of US companies have doubled their records in the past five years. Over 70% of businesses would fail within three weeks of losing paper records to a disaster. Companies without a disaster recovery plan have less than a 10% survival rate, and 90% shut down within two years of losing data. Only 44% successfully recover information after a data recovery event. Contact us to avoid these risks.
*Source: Gartner Group, AIIM, US Dept of Labor, Imaging Magazine, Coopers & Lybrand, StorageCraft

Why We Do It
FACT: DISASTERS HAPPEN.
How would your organization recover if a major disaster or data breech compromised your physical records?
A major disaster or data breach could compromise your physical records, and industry research shows that about 20% of US companies have doubled their records in the past five years. Over 70% of businesses would fail within three weeks of losing paper records to a disaster. Companies without a disaster recovery plan have less than a 10% survival rate, and 90% shut down within two years of losing data. Only 44% successfully recover information after a data recovery event. Contact us to avoid these risks.
*Source: Gartner Group, AIIM, US Dept of Labor, Imaging Magazine, Coopers & Lybrand, StorageCraft

Our Process
Our client-focused process begins with a detailed consultation to understand your needs. From document preparation to precise data capture and digital conversion, we tailor our services to fit your requirements seamlessly, ensuring efficient integration into your existing systems.
Our Process
Our client-focused process begins with a detailed consultation to understand your needs. From document preparation to precise data capture and digital conversion, we tailor our services to fit your requirements seamlessly, ensuring efficient integration into your existing systems.

Benefits of Our Services

Cost
Reduction
Experience significant
savings by streamlining
document management
processes.

Enhanced
Security
Secure document storage
meets federal regulations,
protecting critical
business information.
Operational
Efficiency
Improve workflow and
efficiency with our
advanced scanning and
data management solutions.

Client
Education
Equip your team with
the knowledge to manage
and enhance digital
operations independently.
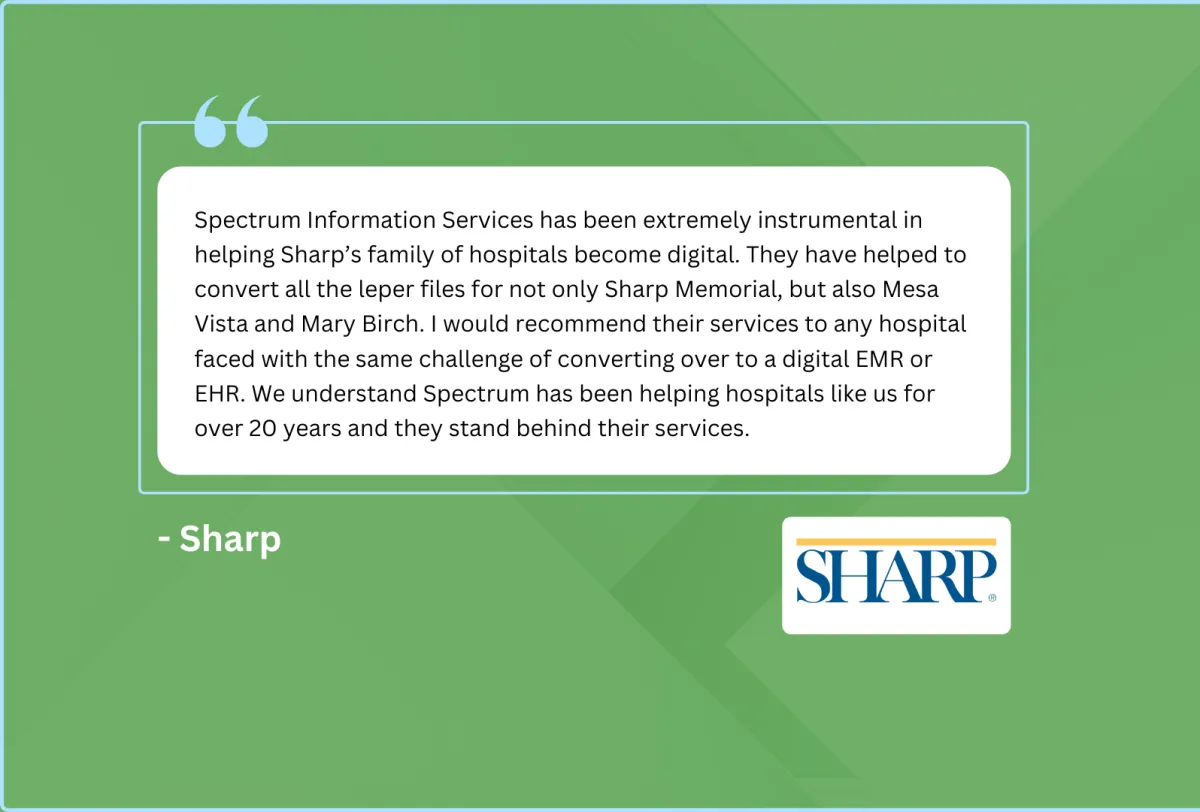
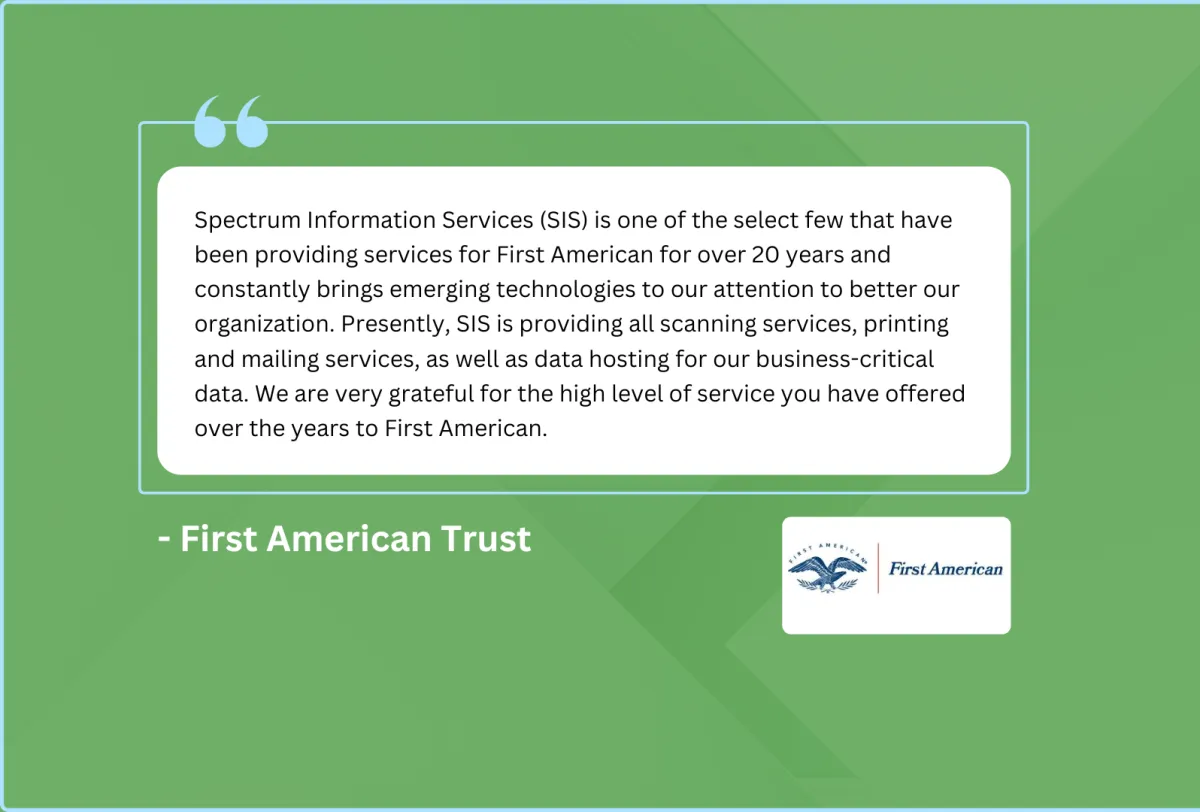
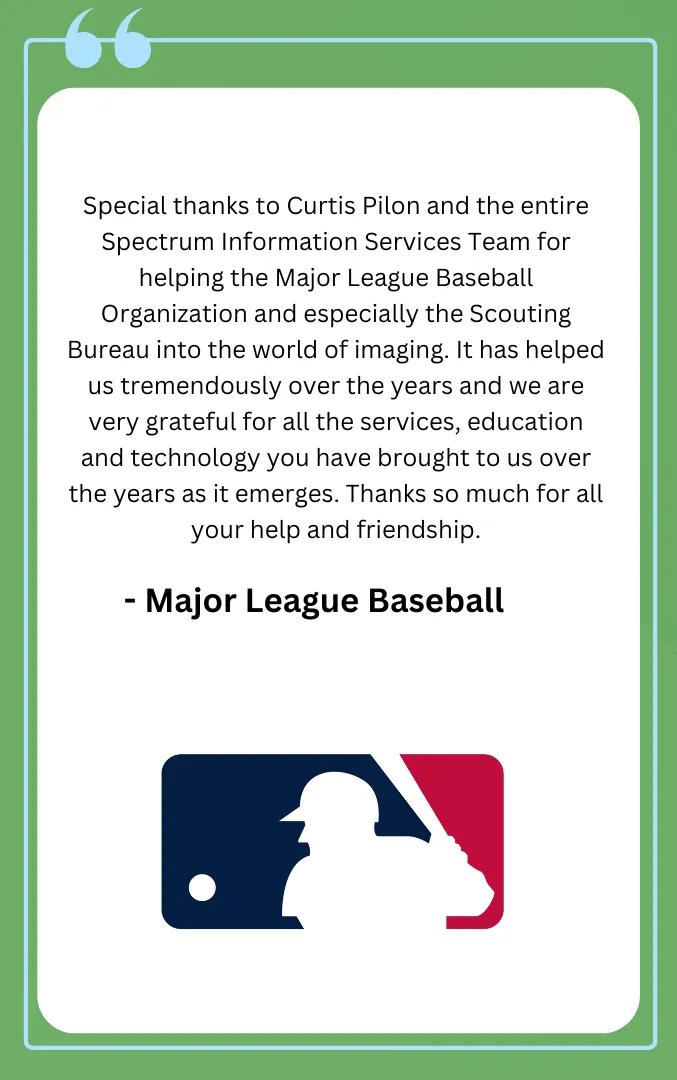
Brands That Trust Our Work